At the beginning of 2020, the sudden pandemic made the opening full of ups and downs. In such an unusual year, we saw joys and sorrows, difficulties and perseverance in the tide of the times. The COVID-19 has brought pressure and challenges to countless companies. One of the important changes is online office.
Under "New Infrastructure" initiatives in China, if the digital transformation of enterprises is a way to upgrade business and supply-side reformation, then the pandemic is undoubtedly a booster for enterprises to accelerate their migration to the cloud. All this not only makes the cloud adoption an efficiency, technical, and business issue but adds a force for rapid response and endogenous reform when facing the risk.
The public cloud, hybrid cloud, and private cloud are rising on the cloud computing market. With the development of the cloud computing industry at different stages, the cloud security has always been the critical consideration of users. The cloud security market continues to grow rapidly in 2020. Security technology has always been improved with the development of information technology and application scenarios. Today we will mainly talk about the trend of Chinese and global cloud security hot technologies in 2020 and future development.
Globe
Container Security Becomes New Hotspot
Under the new situation where 5G and critical infrastructure are gradually being implemented, the business with more agility, rapid implement and intelligent operation has gradually become a common understanding in the industry. New technical architectures and new development models continue to bring more values to users. Container, Kubernetes, DevOps, and microservices have developed fast, and have been actively adopted by a large number of users and developers. At the same time, cloud security technologies, products and solutions for containers and new techniques have also been continuously improved and developed.
Container is a lightweight virtualization technology that can isolate computing, network, and storage on the host, realizing emerging architectures such as microservices. Considering the short life cycle of container, including compilation, transmission, and operation, container security solution provides comprehensive and continuous protection around the entire life cycle of the container.
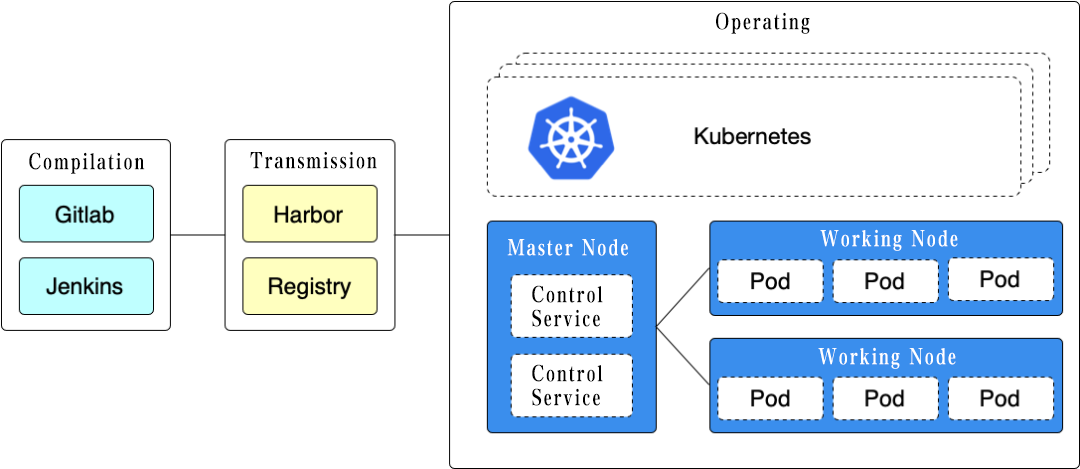
The compilation provides security capabilities such as source code auditing and continuous scanning of container image vulnerabilities. Considering that containers are often combined with the cloud-native development process, container security products are usually integrated with CI/CD tools such as Jenkins, providing security protection for the automatic container compilation.
The transmission involves the security management of the container mirror warehouse server, including the network security of the mirror warehouse server and the periodic mirror vulnerability scanning of the mirror warehouse server. Security products should support a variety of different mirror warehouse server interfaces at this stage for users providing highly adaptable protection capabilities.
The operating of the container is different in operating environment. In a pure container operating environment, it should provide environment compliance inspection, intrusion prevention, microsegmentation, event monitoring, and consistency monitoring. It should provide additional protection if it has orchestration tool. Kubernetes is a mainstream container orchestration tool that has now become a standard. Taking it as an example, it also needs to provide security capabilities such as compliance baseline verification, microservice discovery and governance, and cluster authority management for Kubernetes platform.
SASE New Favorite
SASE (Secure Access Service Edge) was first proposed by Gartner in the article "The Future of Network Security Is in the Cloud". Facing increasingly complex cloud computing environments, SASE provides a policy-based software-defined security protection method with many security capabilities including SWG, CASB, FWaaS, ZTNA, to achieve identity-based dynamic security, which is a cloud-based delivery network solution combined the next-generation wide area network, security, and edge computing.
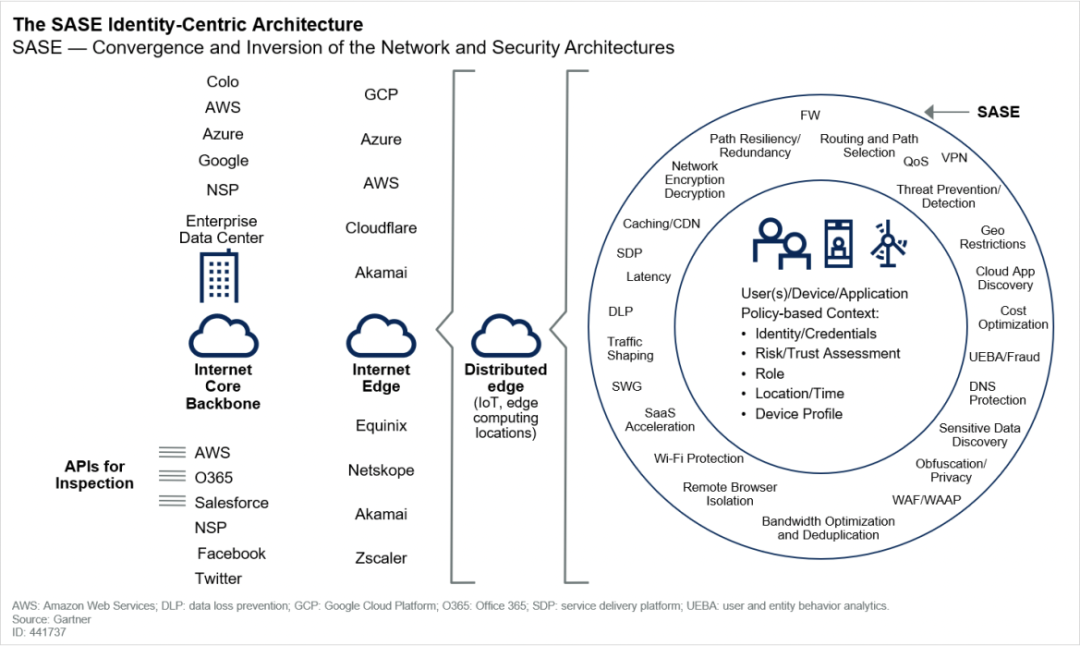
With the promotion of 5G edge computing, especially under the pandemic, the global network architecture has undergone tremendous changes. More and more enterprises use online office models and adopt data center network models. This change in working mode and network mode puts forward more stringent requirements for telecom to perform security management authentication of mobile devices and personal identities, dynamic location identification, strict network control, and rapid and complete delivery of security capabilities. In the SASE solution, the software-defined network capabilities brought by SD-WAN and SDP technologies are fully used, combined with identity authentication technologies such as UEBA, to realize an identity-based zero-trust network infrastructure. At the same time, the SASE solution usually combines edge computing technology to manage and control deployed various security devices and network applications to achieve flexible, dynamic, fast delivery and low-latency comprehensive network security services.
Cloud Security Product Convergence Becomes New Format
In the past two years, CWPP (Cloud Workload Protection Platform), CSPM (Cloud Security Posture Management), CASB (Cloud Access Security Broker) are three security direction promoted by Gartner, focus on cloud workloads, cloud security compliance, and cloud data security. The three have overlapping security capabilities on the basis of complementing each other. CWPP works at the IaaS. CSPM protects IaaS and PaaS, and CASB protects IaaS, PaaS and SaaS. Moreover, with the development of technology and the improvement of product security capabilities, security vendors have integrated core technologies into security products, learning from each other's strengths, and forming comprehensive security solutions and security platforms. The Prisma product line of Palo Alto, an integrated security company, unifies the three cloud security technology products of CWPP, CSPM and CASB to provide comprehensive solutions and a series of cloud security capabilities such as SASE, container security, and microsegmentation. The startup CloudPassage also integrates CWPP, CSPM and CASB technologies, and combines container security protection capabilities to provide a unified cloud security protection platform.
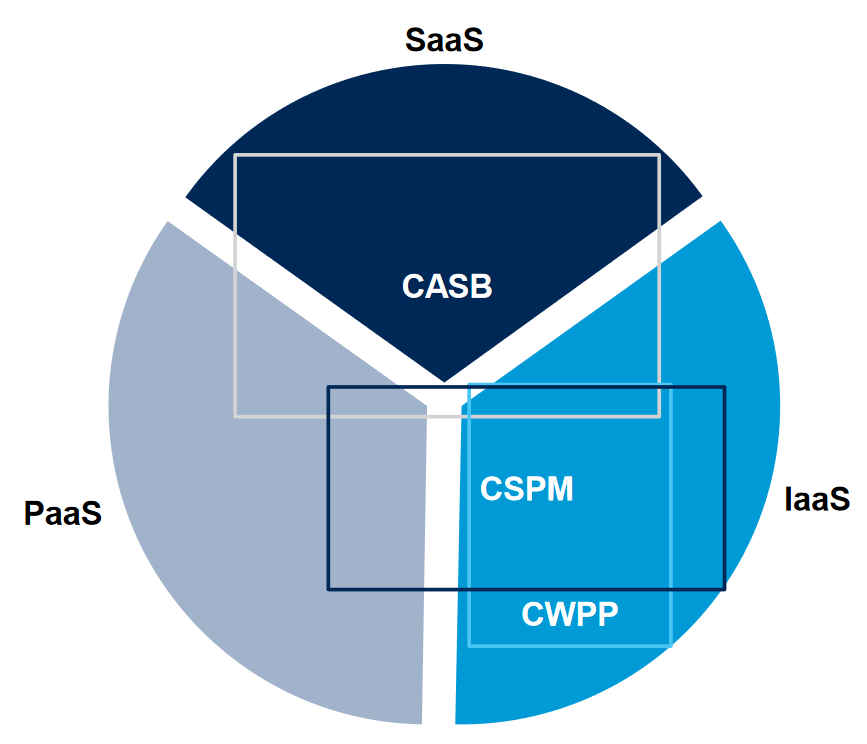
Cloud security products and solutions solve users' cloud security issues at the end. With the maturity of the cloud computing industry, the development of cloud security technology and the deepening of users’ understanding of business security, it is an inevitable trend for cloud security to enter the era of overall solutions. How to provide more comprehensive and in-depth security capabilities and services for cloud users and businesses have become a problem that major cloud security vendors must face.
China
Cloud Native Security Gets More Attention
The term cloud native came into being and emerging during the highly developed process of cloud computing. It usually refers to the fact that developers pay more attention to business development, give full play to the cloud platform's elastic computing, rapid deployment, and on-demand capacity expansion capabilities to build cloud native applications, mainly involving containers, microservices, and DevOps.
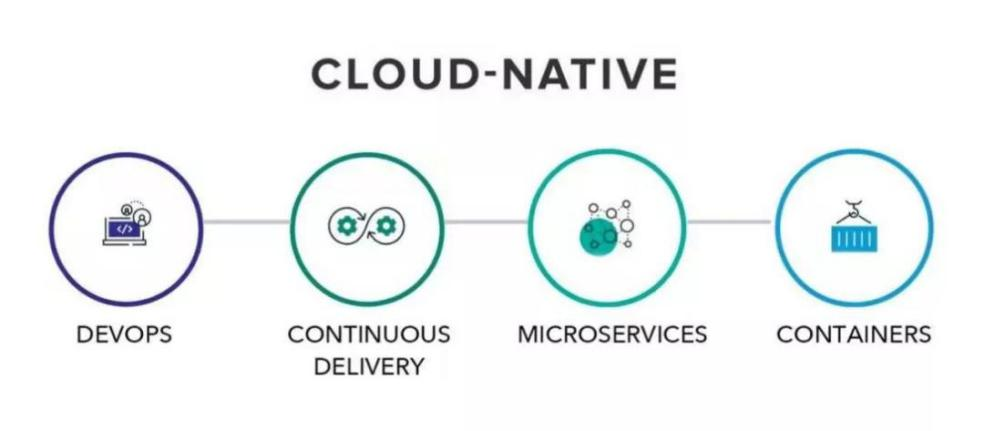
With the development and implementation of 5G, new infrastructure, big data, artificial intelligence and other technologies in recent years, cloud native has become one of the most important forms of cloud business. Many businesses such as government, finance, and enterprises are based on the development and implementation of cloud native concepts. Therefore, the security of cloud-native systems has also become the focus of industry research. Cloud native security is not achieved by a single product, but a security awareness and security system. The concepts include security shift-left, zero trust, DevSecOps. The technologies and products involve source code auditing, container security, microservice security, microsegmentation, data leakage prevention, identity authentication.
Venustech reviewed the China cybersecurity industry in 2020 found that the current cloud-native security is not only at the conceptual stage but have deployed products and solutions. Many related security startups have emerged in China. Established security companies are also making efforts in this area, which also fully shows the importance of cloud-native security.
Considering the convenience of cloud-native architecture for business developers, the design of cloud-native products needs to fully manage the cloud business and the architecture of the cloud itself, realize the capability of security as a service, integrate security into the development of cloud business, and run throughout the software life cycle, continuous delivery and deployment as business.
Cloud Security Convergence Becomes New Format
Technology always leads to the same goal by different routes. Just like the international cloud security situation in 2020, the China cloud security industry also presents an integration trend. It is found that users have a deeper understanding of cloud computing environment and business security, put forward many cloud security requirements that combine cloud architecture and business characteristics. Secondly, a single product has been unable to meet the security requirements of users on the cloud. A unified security system and solutions with more comprehensive and stronger security capabilities are required. Therefore, in some projects, a combination of multiple security product capabilities has become one of the most mainstream delivery forms.
Taking CWPP as an example, many Chinese manufacturers integrate CWPP products with cloud baseline inspection capabilities, and CSPM capability. At the same time, some security vendors and cloud suppliers have also invested in container security, combining container security with existing products to form a total solution. With the implementation of Classified Protection 2.0 in China, various standards issued by Chinese ministries and commissions have gradually refined the security requirements and capabilities on the cloud, all of which make standard requirements for comprehensive cloud security solutions. Therefore, we believe that cloud security product integration has and will become one of the most important development directions in the future.
Private Cloud Security Era
Unlike the international cloud computing environment, the China private cloud market is larger. According to the "Cloud Computing Development White Paper 2020" issued by CAICT (China Academy of Information and Communications Technology), it was predicted that the China private cloud market will reach RMB 79.12 billion in 2020. Therefore, the private cloud security market occupies a large proportion in China cloud security market. According to market demand analysis in 2020, users will have more demand for multi-cloud solutions. Most users' data centers have multi-cloud and heterogeneous cloud architectures. The demand for private cloud solutions in a multi-cloud environment is prominent.
Taking resource pool solutions in private clouds as an example, most resource pool solution vendors have already supported the security management of multi-cloud and heterogeneous clouds for multi-location and multi-data center. Under such an architecture, the traffic on the cloud does not need to be directed to the same area for centralized processing. The network latency caused by security services is reduced by edge defense. Meanwhile, telecoms have multi-vendor cloud platforms. The adaptation and integration of different cloud platforms has gradually become the industry standard.
Future of the Cloud
New Products and Solutions Around the New Generation of Regulation and Compliance System Will Become a New Direction
In 2020, with the implementation of Classified Protection 2.0 in China, various ministries and commissions will gradually introduce security standards and regulations and industry security requirements for cloud security. Regardless of the breadth or accuracy of security capabilities, cloud security products need to be self-improved. The cloud security industry will also be adjusted under the new regulations. This is a challenge and opportunity for the security industry. All security companies will compete under new compliance system where users will acquire greater security services and security capabilities.
Cloud Security Product for Business Will Compete In the Depth of Security Capability
In recent years, the number of cloud security products has continued to grow, and competition has become increasingly fierce. However, product homogeneity has become more apparent. In the foreseeable future, differentiation in product security capability will become a powerful advantage. Cloud security companies need to find the direction of differentiated development of security services. First, companies need to improve the depth, precision, and breadth of cloud security technologies, and form an effective security closed loop. Secondly, it is a new topic and challenge for security enterprises to propose new comprehensive security solutions under new scenarios such as 5G, new infrastructure, big data, and artificial intelligence.
The New Generation of Cloud Security Technology Under the New Cloud Architecture Will Open Up New Battlefield
The eternal thing is change, which is equally applicable to the cloud security industry, technology, and business. The development of cloud computing has produced a variety of new technologies and new architectures. Fresh concepts such as containers, serverless, and DevOps have become new hotspots in the cloud industry. The accompanying solutions must be to solve related security issues. Whether it is traditional security company, or startup, or cloud provider, they have invested in these emerging fields and are forming related security products. It can be clearly seen that China security industry is continuously upgrading. Based on ensuring compliance, cloud security is evolving in the direction of elementalization, actual combat, and servitization development for network protection requirements and new infrastructure business development.
Have a question? We're here to help.
Please send an email to overseas@venustech.com.cn
Or you can fill out the form below and we will get in touch with you soon.
Thank you for your interest in Venustech.