
Venusense Unified Security Management (USM) is a new generation of big data security management platform developed by Venustech Taihe within emerged technologies accumulation of decade. It uses big data processing technology to reconstruct the traditional security management platform, data-driven, providing stronger data analysis performance, richer interactive analysis functions, and becoming a security guard tool for users.
Adopt Big Data Security Analysis Architecture
Combining CupidMQ message bus with independent patent and CupidDB non-relational database technology, and build streaming analysis, continuous aggregation, interactive analysis, full text retrieval, playback engine, provide high-performance security analysis capability. Flexible and convenient deployment which supports horizontal elastic expansion.
Business-Oriented Unified Security Management
USM has built-in business modeling tools, user can build business topology which reflects the asset composition of the business support system, and automatically build a business health indicator system, from business performance and availability, business vulnerability and business threats to calculate the health of the business.
All-Round IT System Performance and Availability Monitoring
USM can perform real-time, fine-grained operational monitoring of various IT assets across the entire network, detect faults in time, and perform location and alert response to ensure the availability of important business information system and business continuity, and vividly show the user's network topology.
Intelligent Security Event Correlation Analysis and Traffic Analysis
Make use of advanced intelligent event correlation analysis engine, USM conduct security event correlation analysis on all normalized log in real time without interruption. The system provides users with three event correlation analysis technologies, rule-based correlation analysis, context-based correlation analysis, and behavior-based correlation analysis. Through the capture, generation and intelligent analysis of business network traffic information, the traffic profile is established to identify asset attributes, detect business traffic abnormality, and inspect compliance, support cross analysis and traceability of traffic and security events.
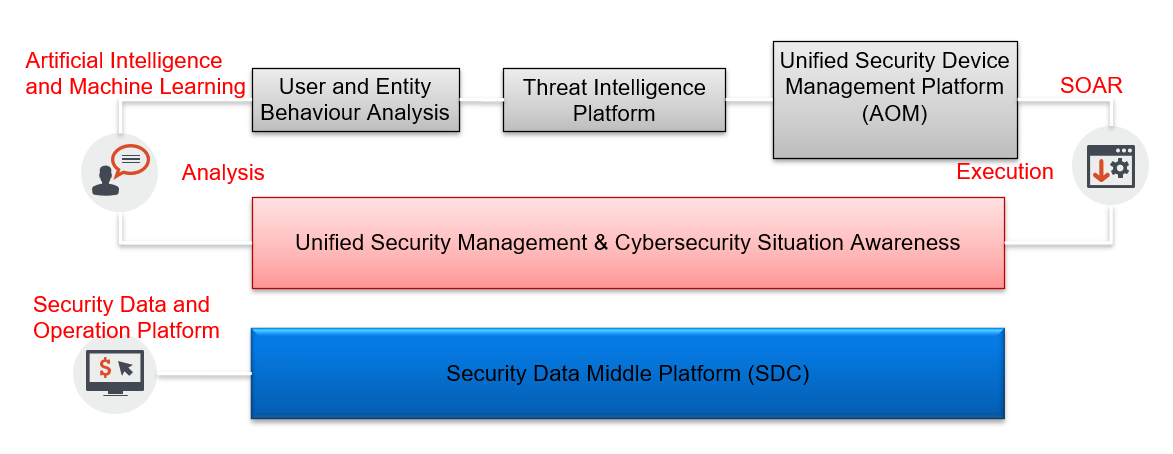
User and Entity Behavior Analysis
USM provides user and entity behavior analysis (UEBA) and portrait capabilities. UEBA uses machine learning and deep learning to establish a baseline for user and entity object behavior and monitor deviations. Provide a wealth of detection algorithms. The advanced threat modeling covers various scenarios of the Kill-Chain; the abnormal user modeling contains login abnormity, file resource access abnormity, account abnormity, email attachment abnormity, and unauthorized operation. Behavior portraits of users and entities can automatically provide evidence for security incidents, clearly display the development and movement of abnormal behaviors related to this incident over time. Provide topic-oriented automated analysis functions which can automatically correlate related alerts and draw attack diagrams, directly show high-risk personnel and equipment, attack sources, and attack paths to accelerate the diagnosis and judgment of security incidents.
Threat Hunting Weapon For Security Analyst
USM provides a set of powerful tools for security analysts to conduct threat hunting and data analysis, enabling security analysts to operate freely in the face of vast amounts of security data, and to capture attention from massive incidents and threats.
Integration and Traceability of Threat Intelligence
USM supports open source intelligence collection capability. It can also integrate data from third-party threat intelligence providers. The types of intelligence collected include malicious IP/URL/DNS/E-mail, which could be used as inputs of correlation analysis, as well as intelligence tracing.
Active and Passive Security Management and Early Warning
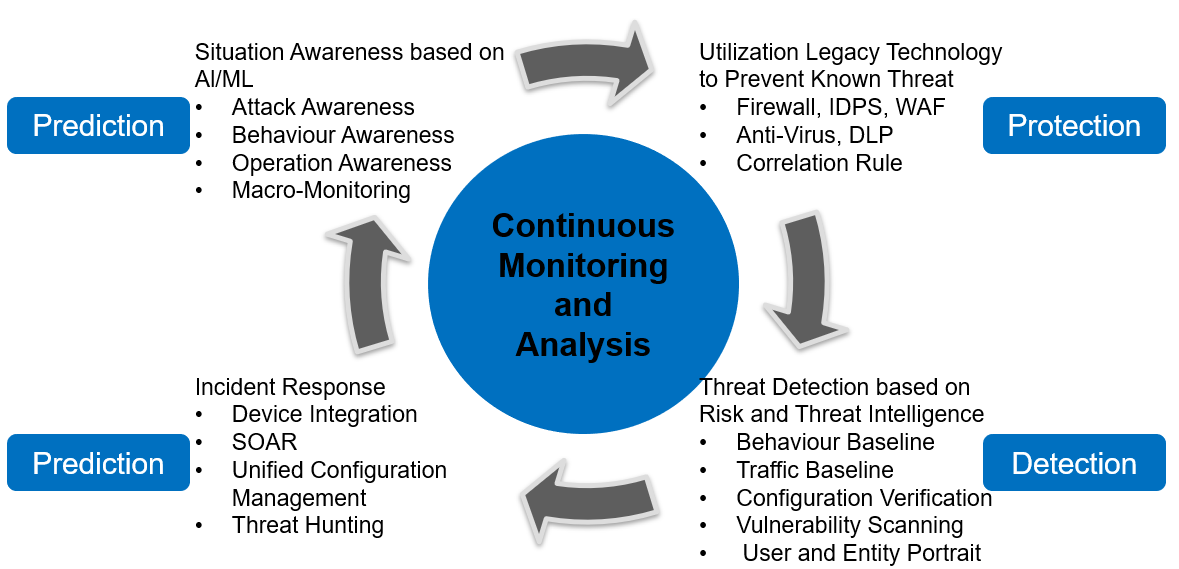
USM introduces an active management procedure. Through security threat early warning management, active vulnerability scanning management, cooperation with security inspection, and vulnerability intelligence analysis, it can learn in advance of possible attacks and threats, and the scope of impact including security vulnerabilities and configuration flaws in assets and business systems. Help managers to take precautions and be able to proactively conduct security management before threats occur.
Multidimensional Security Situational Awareness Presentation
The situational awareness module of USM is an overview of the comprehensive situation in the user's business environment, including asset posture, weakness posture, and attack posture. Enable users to control the macro security and risk posture, understand the current attack posture, comprehensively grasp the security risks of assets and services in the network, identify the threat posture of the protected object, hold the trend of attacks, locate the source of the attack and warn of potential threats.
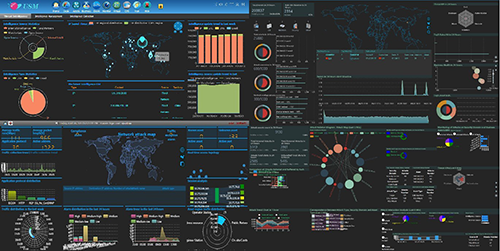
Customized Large-Screen Visualization
USM provides a visualization designer, which can be freely configured according to the resolution display requirements of different specifications, and set the screen resolution boundary line and remind, the font and the background color. Built-in more than 100 visual chart components such as 3D, GIS, data graphs and commonly used number tables. User can drag and drop the chart components to arrange, zoom, filter, combine and match to build a large-screen visual display page.
Have a question? We're here to help.
Please send an email to overseas@venustech.com.cn
Or you can fill out the form below and we will get in touch with you soon.
Thank you for your interest in Venustech.