

Venusense NTA(Network Traffic Analysis) product adopts big data architecture, based on full traffic data, combined asset data, configure and vulnerability data, and threat intelligence, form a baseline of access behavior by building a self-learning behavior model to generate network perception capabilities. Reveal internal threat with the help of attack chain model and use the diamond model to perform further investigation. Central visual and statistic through the comprehensive processing and correlation analysis of multi-dimensional data. Achieve threat prewarning integrate with threat intelligence. Help to complete rapid response by providing disposal suggestions.
● Full Traffic Collection: combine DFI(Deep Flow Inspection)&DPI(Deep Packet Inspection) technology to realize the collection and analysis of traffic, application metadata, transmission files, raw packet.
● Network Awareness Baseline: establish a baseline of assets, services, and access relationships, and provide visualization of network traffic.
● Latent Threat Discovery: use attack chain model to uncover the internal threats and build diamond model to forensics and investigate the compromised host.
● External Attack Discovery: detect DDoS attacks from the deviation of abnormal traffic behavior.
● Internal Access Audit: disclose unauthorized traffic by correlation rule engine.
● Integration: conduct vulnerability management using asset collector, vulnerability scanner and configuration inspection.
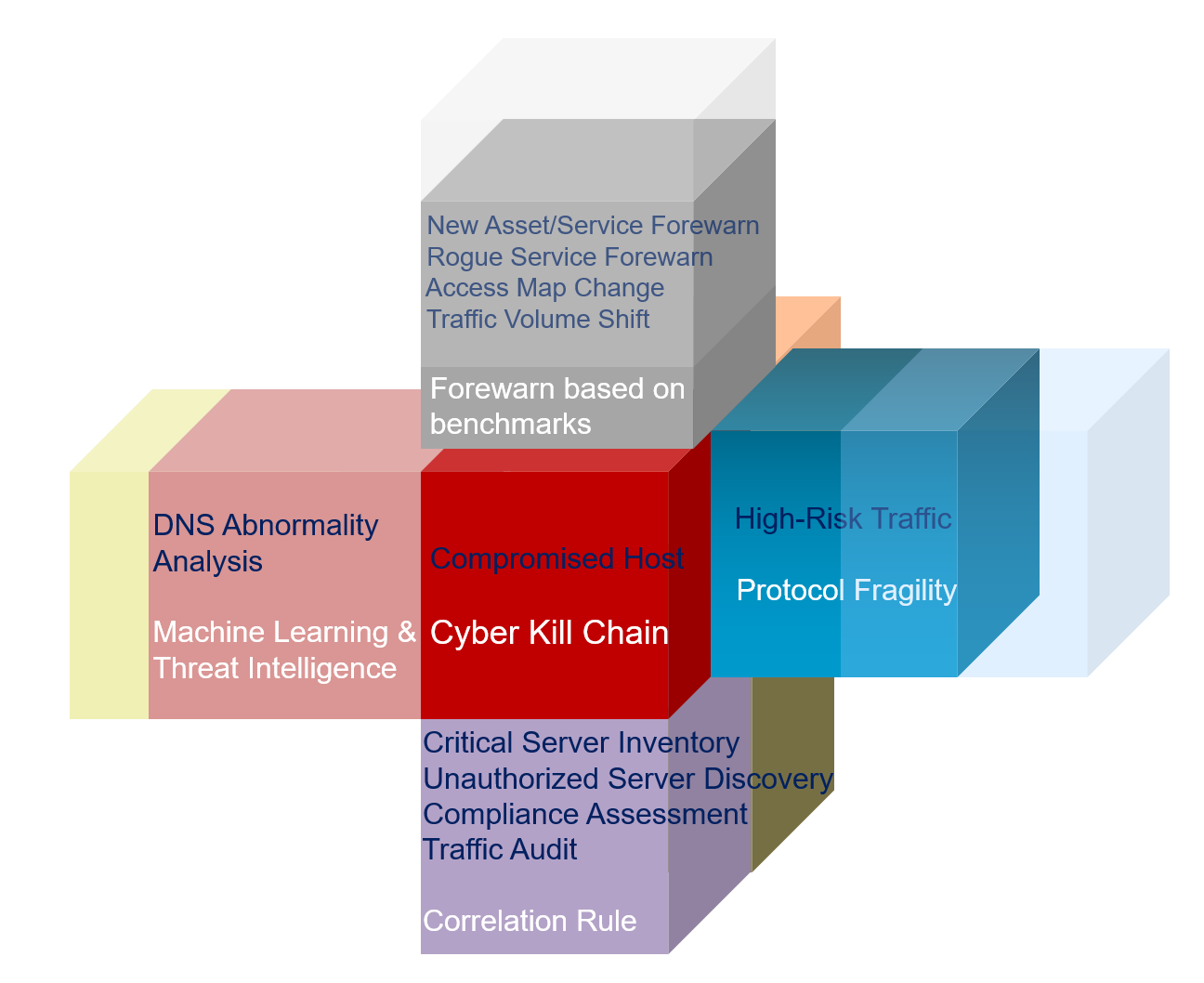
● Solve the threat of breaking through the perimeter and entering the intranet.
● Realize mass storage of session data, application protocol metadata, and original PCAP messages.
● Fastly locate issues and respond quickly and complete the closed loop of threat processing to put to use correlation analysis, behavior analysis, AI analysis engine, and the security incident response recommendations of the knowledge base.
● Support multiple access of various *Flow data and port mirroring.
● Support all-in-one deployment, as well as horizontal flexible deployment of collectors and storage nodes.
Compromised Host Monitoring
In the case of hidden attack features and unequal attack and defense, more and more attacks have crossed the perimeter protection equipment. The feature-based detection tools have begun to be stretched. It has also caused new threats to emerge, futile borders, and insidious risks.
Adopt revised Cyber Kill Chain forming five stages of sniffing, intrusion, C&C control, lateral proliferation, and outreach detection, which combined the dynamics of the attack process and continuous movement in perception engine.
Through the analysis of the reconnaissance and sniffing stage, discover attack path and target. Reinforce the perimeter protection or endpoint security to keep the bad actor out of the first line of protection.
Display network access permission acquisition and escalation, in order to introduce attack weapons, in the resident C&C control phase. Disconnect the bridge of infected points and remote control to prevent greater loss.
In the execution stage of lateral movement and data transmission, pay attention to how the attacker fulfils the final goal, and stop the malicious behavior of the attacker and minimize losses.
Quickly Respond to Notification and Warning from Supervisory Unit
At present, the investigation and forensics collection has become a necessary part of response and disposal. Accordingly, hackers will try their best to erase the log information left behind such as Apache, MYSQL, PHP, Linux. Tool and software that can hide the traces of their attacks emerge. The network traffic data has the characteristic of leaving traces naturally. A system that provides traffic context will become the best choice for user investigation and forensics collection.
Venusense NTA adopts big data architecture to support rapid query and scalable storage of massive traffic data. The acquisition of attack information will no longer be limited to the security log, and more traffic context data is also required. Perform correlation analysis of security device logs, traffic session, application protocol metadata, original PCAP messages to complete problem confirmation and attack source tracing, so as to quickly locate the problem device and form a closed loop.
Have a question? We're here to help.
Please send an email to overseas@venustech.com.cn
Or you can fill out the form below and we will get in touch with you soon.
Thank you for your interest in Venustech.