In the era of big data, data is the most important asset. In the face of frequent data security incidents, we can not help thinking about how to do in the construction of data security for service providers, enterprises or government that particularly care about data assets? Taking the recent case of database deletion as an example, this article analyzes three existing solutions for data security, and puts forward a special operation solution for data security of Venustech to help users solve the data security problems.
In the Era of Big Data, Data is the Most Important Asset.
From a personal point of view, food, clothing, housing and transportation will generate data, including the most basic personal information and historical consumption records. If the data is stolen, it will cause property loss to individuals and even serious consequences to society.
From the perspective of enterprises, data, especially business data, is the key part of market competition. It is the most basic responsibility to protect the data security of users, which is related to the development and reputation of enterprises.
Therefore, Whatever Views are, Data Security Protection is Essential.
Recently, a SaaS service provider of e-commerce retail, catering, takeaway, beauty industry and liquor and travel has suffered from database deletion by internal staff due to the failure of data security protection. It has also offered an apology and compensated its users for RMB 150 million. In the capital market, the evaporated market value is more than RMB 2 billion, and the potential loss is even more incalculable.
We can't help thinking
For service providers, enterprises or government
How can we do in the construction of data security?
Analysis of Existing Data Security Solutions
In recent years, data security has gradually come to people's vision and is valued by everyone.It has occurred many data security solutions. There are roughly three types:
1. Data Security Construction Based on Data Life Cycle
Data life cycle is a term at the level of data governance, which refers to the whole process of data production, collection, archiving and destruction. Now, many data security solutions have involved. However, the data life cycle is more suitable for the management based on files. When it is applied to business data and data sharing, it is difficult to realize. It is very likely to change the whole business process and business system in order to solve one problem, which results in problems such as low input-output ratio, cumbersome process and difficult to control. The data security will be better guaranteed if we control and manage whole data life cycle.
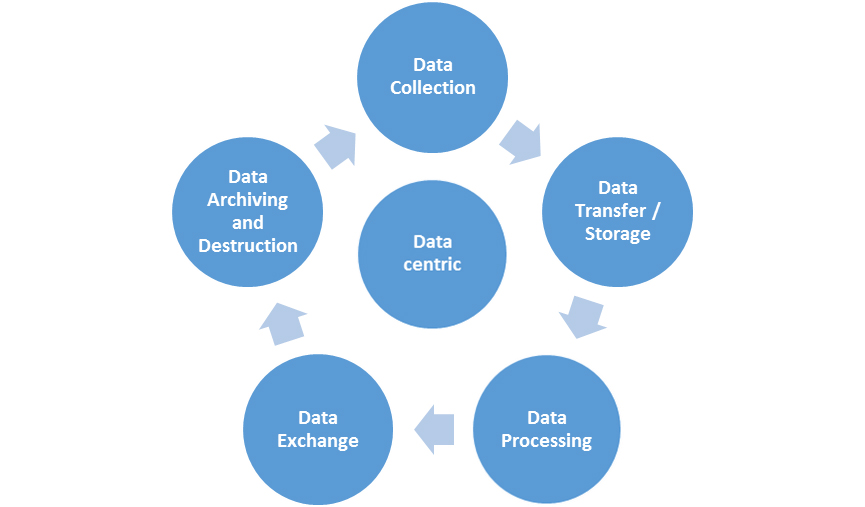
Full life Cycle of Data
2. Gartner Data Security Governance Framework
Gartner began to focus on data security governance in 2017, and proposed a data security governance framework, which is divided into five steps:
1) The balance between business needs and security (risk, threat, compliance).
2) Data priority, data classification, so as to implement reasonable security means for different levels of data.
3) Develop policies to reduce security risks.
4) Implement security tools and deploy security control points (including Crypto encryption, Data Centric Audit and Protection, Data Leakage Prevention, Cloud Access Security Broker, Identity and Assessment Management, User and Entity Behavior Analysis).
5) Policy configuration synchronization.
Although Gartner's data security governance framework makes a systematicalplanning for data security from compliance, risk and policy.But it ignores the impact of time on data security risk, and data security changes with the change of business conditions. Therefore, we should pay attention to not only the overall design, but also the continuous risk prevention and monitoring.
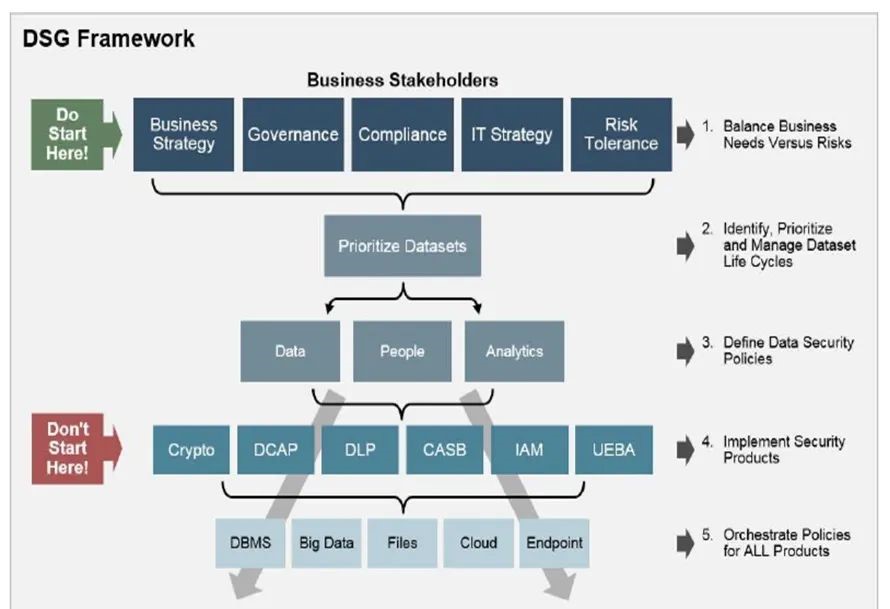
Gartner Data Security Governance Framework
3. Solve Data Security Problems from the Perspective of Space
At present, many data security solution providers will solve problems from other perspectives in order to avoid the complexity and realization problems brought by life cycle solutions. Such solutions are to exchange space for time and solve data security problems from scenarios and identities as we said.
The data security scenarios are distinguished from different roles and user, including maintenance, data export, data process, etc. It should create different policies and roles to ensure data scenario security.
This way not only absorbs the essence of Gartner's data security, but also solves the implementation problem of data life cycle. For users, it can also play a good role in data security control, but it still cannot adapt to business development.
Special Operation Solution for Data Security of Venustech
As a leading enterprise in the information security industry, Venustech has a complete data security product system. Through intensive work in security operation, it summarizes a set of special operation solution for data security. This solution is oriented to user business data, based on sensitive information and data asset governance, with data security risk prevention and control as the goal and scenario data security management and control as the means, taking into account the audit of each stage of data life cycle, as well as closed-loop data security management and control .
This database deletion incident is a problem from personnel authority management. We should do a better job in fine-grained security control over the data security of scenario (maintenance /R &D), and carry out continuous monitoring and early warning of data security risks, so as to quickly block and respond to abnormal behaviors.
Special operation solution for data security of Venustech has the advantages of Venustech products (such as IAM, data masking system, data encryption system, data leakage prevention, database audit and other products) and solutions related to data security governance. It also integrates \ security operation, from compliance, asset investigation, sensitive traceability, risk management and control and continuous risk monitoring operation and other aspects to help users solve data security problems.
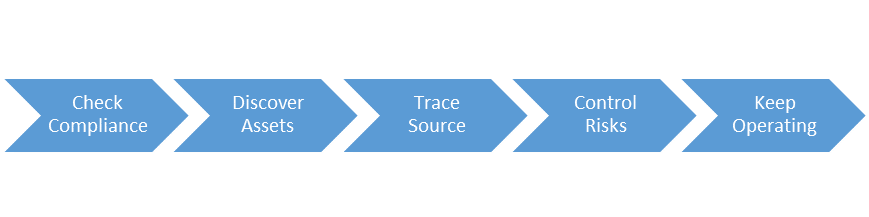
Value of Special Operation Solution for Data Security of Venustech
● Check compliance: Security compliance is the premise to ensure the security compliance of business data.
● Discover assets: Take user business data as the core, clarify their own data assets, and ensure the discovery, classification of sensitive information.
● Trace source: With the method of flow and behavior analysis, trace and analyze the abnormal data access behavior to ensure the traceability of sensitive data.
● Control risks: Take space and time polices as dimensions to prevent and control data security risks.
● Keep operating: With the help of data security operation, guarantee risk monitoring of business data continuity.
At present, the enterprise that suffered the database deletion event has carried out self-examination in the internal system and invited external data security experts to evaluate together, and formulated the data security solution including the comprehensive reinforcement and rectification of the data security management mechanism, the strong governance of the operation and maintenance platform, etc.. Special operation solution for data security of Venustech is a reliable choice which conforms to user business feasibly, manages and controls the data security accurately, prevent and control data security risks effectively.
Have a question? We're here to help.
Please send an email to overseas@venustech.com.cn
Or you can fill out the form below and we will get in touch with you soon.
Thank you for your interest in Venustech.