When mentioning Internet celebrity, the first things that come to mind are Internet celebrity peopleperson, Internet celebrity shops and Internet celebrity snacks, etc.
Today, I'm going to talk about the different Internet celebrities for you.
Ten Categories of "Internet celebrity" Vulnerabilities in the Finance Industry
Based on finance industry research and project practice summary, Venustech summarized ten categories of vulnerabilities with high "activity" in financial industry in recent years (ranking in no particular order), and put forward some safety suggestions for the reference of users in financial industry.
★ Business Logic Vulnerability
The finance industry is closely related to capital flow. Internet finance, online banking, mobile payment and other emerging models have tended to be normalized, which puts forward higher requirements for system or website design. If there are defects in some functional modules, such as capital transaction, the resulting business logic vulnerabilities are easy to cause significant benefit losses to financial institutions.
The Problems of Business Logic are as Follows:
● It is allowed to tamper with the credits, amount, quantity and payee information in the transaction process.
● The verification code can be obtained directly through the web page.
● Key operations are in a lack of secondary authentication.
● The unit price of the purchased goods can be controlled by client
● The transfer and payment amount can be negative value.
● Reset any user's account and password.
Security Advice from Venustech
For transaction business, financial institutions should consider the problems of data tampering prevention and replay attack prevention, etc. Key parameters such as unit price, amount and other parameters need to be generated in the server or secondary authentication is enabled for the data submitted by the client.
★ Data Leakage Vulnerability
In recent years, cyber security attacks on financial institutions have become increasingly frequentBank accounts, personal privacy and other sensitive information are stolen from time to time, causing unpredictable losses to financial institutions, enterprises and individuals. How to protect user privacy and data security, and how to prevent major data leakage events in the finance industry are still the focus of network security.
Major Data Leakage Events in the Finance Industry in Recent Years
Date | Event | Number of Leaked Data |
July 2017 | Data leakage of Equifax, the credit institution of the United States | 143 million |
October 2017 | Large amount of sensitive information leaked from Accenture server | 1,900 million |
November 2017 | Large-scale data leakage of Uber | 57 million |
June 2018 | Resume leakage of 51Job | 1.95 million |
August 2018 | Information leakage of Huazhu hotels | 500 million |
October 2018 | User privacy data disclosure of Cathay Pacific | 9.4 million |
May 2019 | Leakage of insurance documents of FAFC, including bank account number, statements of account, mortgage loans and tax records, etc. | Hundreds of millions |
June 2019 | Data Leakage of Desjardins Group, the largest association of credit cooperatives in North America | 4.2 million |
December 2019 | E-commerce website server log and user data can be accessed directly | 1.3TB |
Security Advice from Venustech
At present, financial institutions pay more attention to information and data security, and the security protection of business system is more rigorous. It is recommended that financial institutions regularly conduct training on employees' personal information security awareness. Meanwhile, Venusense Data Leakage System (DLP)can help managers to find potential leakage risks, so as to effectively reduce the possibility of data leakage.
★ Middleware Vulnerability
Most financial institutions use Apache tomact, struts 2, Weblogic, ngnix and other middleware for system development.The third-party component vulnerabilities are often the key point which attackers attempt to mine, requiring great attention to be paid.
Vulnerability | Risk | InfluencedVersion |
CVE-2019-2615 | This vulnerability allows an attacker to read arbitrary files in a WebLogic Server with a known username and password | WebLogic 10.3.6.0 WebLogic 12.1.3.0 WebLogic 12.2.1.2 WebLogic 12.2.1.3 |
CVE-2019-2618 | The vulnerability mainly exploits the DeploymentService interface in WebLogic component, which supports uploading arbitrary files to the server. The attacker breaks the OAM (Oracle Access Management) authentication, sets the wl-request-type parameter to app upload, constructs the POST request package in the file upload format, uploads the JavaServer Pages Trojan file, and then obtains the permissions of the whole server. | WebLogic 10.3.6.0 WebLogic 12.1.3.0 WebLogic 12.2.1.3 |
CVE-2019-2725 | An attacker can use this vulnerability to execute commands remotely without authorization | WebLogic 10.X WebLogic 12.1.3 |
CNNVD-201906-596 | Due to incomplete patching of historical vulnerability (CVE-2019-2725), the patching can be bypassed and the vulnerability can still be exploited | WebLogic 10.X WebLogic 12.1.3.0 |
CVE-2019-2647 | By using this vulnerability, an attacker can encapsulate the payload in T3 protocol without authorization. By deserializing the payload in T3 protocol, a remote Blind XXE attack can be carried out on the Weblogic component with the vulnerability | WebLogic 10.3.6.0 WebLogic 12.1.3.0 WebLogic 12.2.1.2 WebLogic 12.2.1.3 |
CVE-2019-2891 | An attacker can attack WebLogic Server by sending HTTP request without authorization Once it is successfully utilized, the target WebLogic Server can be controlled. | WebLogic 10.3.6.0.0 WebLogic 12.1.3.0.0 WebLogic 12.2.1.3.0 |
Security Advice from Venustech
Administrators should pay attention to the related vulnerabilities of middleware in real time and update or patch the middleware with vulnerabilities in time. Venustech can provide users with VenusenseVulnerability Scanning and Management System, check, evaluate and manage the vulnerability of operating system and network equipment, help customer to discover relevant vulnerabilities in time, and reduce the risk of security risks.
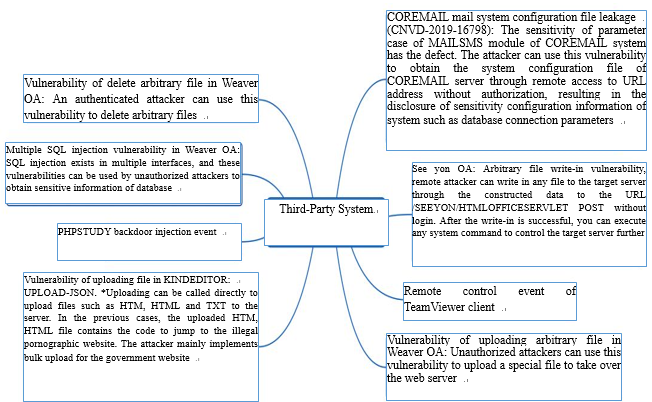
★ Third-Party System Vulnerability
With the development of Internet finance, different types of financial institutions use a lot of third-party applications or frameworks in the system development, such as OA system, e-mail system, in order to improve the efficiency of financial services, , which also makes third-party system vulnerabilities a more common attack option.
Venustech'sSecurity Advice from Venustech
It is recommended that financial institutions should pay real-time attention to the update of the used third-party application system and update it as soon as possible to reduce the potential security hazards caused by the third-party system vulnerabilities.
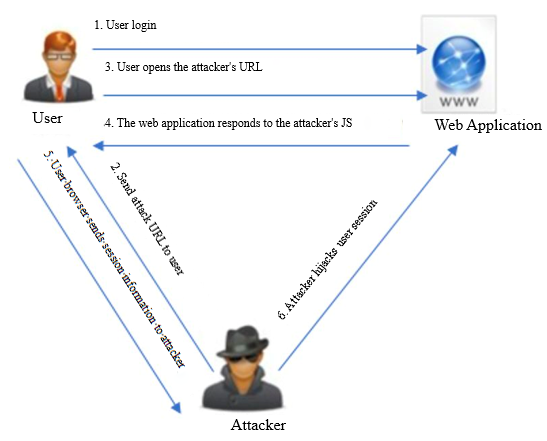
★ Cross-Site Scripting Attack Vulnerability
Cross-site scripting attack vulnerability is one of the most common web application vulnerabilities. When users browse the web pages embedded with malicious code, the malicious code will be executed on the user's browser, which steal the administrator's cookie, tamper with the web page or jump to the phishing page, malicious system, etc.
Security Advice from Venustech
It is recommended to filter special characters, distrust any content submitted by users, and detect the content entered by users.
★ Cross Site Request Forgery (CSRF) Vulnerability
Cross Site Request Forgery Vulnerability refers to an attacker sending a request to the server by the user, resulting in the user information being forced to be modified, and even causing a worm attack. The vulnerability can cause the leakage of sensitive information of customers in the finance industry, unauthorized operation of customer accounts, CSRF worms and other hazards.
vulnerability found in modifying personal information | Make attack POC | Entice the user to execute the URL after logging into the system | After clicking, the form will be submitted automatically and the user information will be tampered with |
Security Advice from Venustech
It is recommended to check the Referer field and add token for verification to avoid CSRF vulnerability.
★ OS Vulnerability
Windows and Linux are the mainstream operating systems. If the patches are not updated in time, once they are used by attackers, it will cause malicious code execution, privilege promotion and other problems, resulting in important data loss and system damage.
Vulnerability Number | Risk | Influenced Version |
CVE-2019-0708 | The vulnerability exists in the way the RDP service handling incoming requests. An attacker can send a malicious request to the RDP service. Due to improper request processing, the target is to execute the malicious code injected into the request. CVE-2019-0708 is a pre-identity | Microsoft Windows XP 0 Microsoft Windows Server 2008 R2 for x64-based Systems SP1 Microsoft Windows Server 2008 R2 for Itanium-based Systems SP1 Microsoft Windows Server2008 for x64-based Systems SP2 Microsoft Windows Server 2008 for Itanium-based Systems SP2 Microsoft Windows Server 2008 for 32 -bit Systems SP2 Microsoft Windows Server 2003 0 Microsoft Windows 7 for x64-based Systems SP1 Microsoft Windows 7 for 32-bit Systems SP1 |
CVE-2019-9510 | The vulnerability could lead to an attacker hijacking an existing remote desktop services session to gain access to the computer. The Oday can be used to bypass the lock screen of Windows devices, even if two-factor authentication such as Duo Security MFA. Other login configurations that the organization may set can also be bypassed | Windows 10 1803 or Server 2019 or updated system |
CVE-2019-1181 CVE-2019-1182 CVE-2019-1222 CVE-2019-1226 | An attacker can obtain remote code execution permission on the target system by constructing a malicious special RDP request to trigger vulnerability. According to Microsoft announcement, the vulnerability is pre-identity authentication, no user interaction is required, which means that the vulnerability may be exploited by worms. | Windows 7 SP1, Windows Server 2008 R2 SP1. Windows Server 2012. Windows 8.1, Windows Server 2012 R2, and all supported windows 10 versions, including service version |
CVE-2019-1333 | When a user connects to a malicious server, the attacker can execute arbitrary code on the computer connecting to the client. The attacker may install programs, view, change, or delete data, or create new accounts with full user privileges. | Windows 10; Windows 7; Windows 8.l; Windows Server 2008 SP2, SPl; Windows Server 2012; Windows Server 2012 R2: Windows Server 2016; Windows Server 2019: Windows Server, version 1803 Windows Server, version 1903 |
CVE-2019-13272 | It can be used for ptracesuid binary file and get root privileges | Linux Kernel < 5.1.17 |
Security Advice from Venustech
It is recommended to use the Venusense Vulnerability Scanning and Management System to analyze the vulnerability of the operating system, find out and fix them in time.
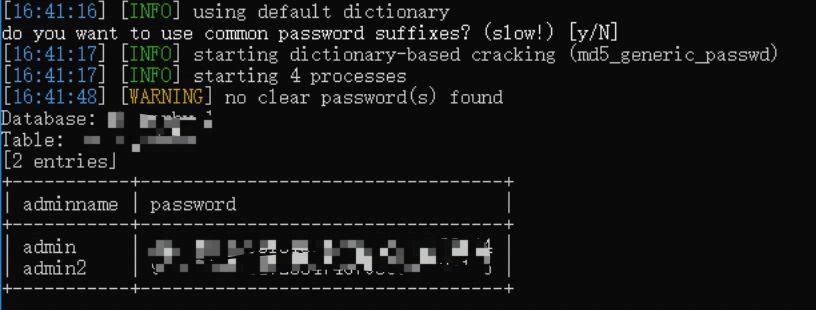
★ SQL Injection Vulnerability
As a means of database attack and Web application attack, SQL injection is often regarded as a breakthrough to the intranet by attackers. In the process of project practice, the attacker obtains the relevant data of the system by SQL injection vulnerability, logs in the background management system, and then conducts penetration test on the background management system.
Security Advice from Venustech
It is recommended to use the parameterized query method for SQL query, filter special characters, strictly control the permissions of database users, and encrypt the core business database information. In addition, VenusenseDatabase Audit System can be used to effectively conduct real-time alert and audit illegal database access behavior, database intrusion behavior, and illegal access behavior, so as to timely discover the risk of violations and effectively protect the database security.
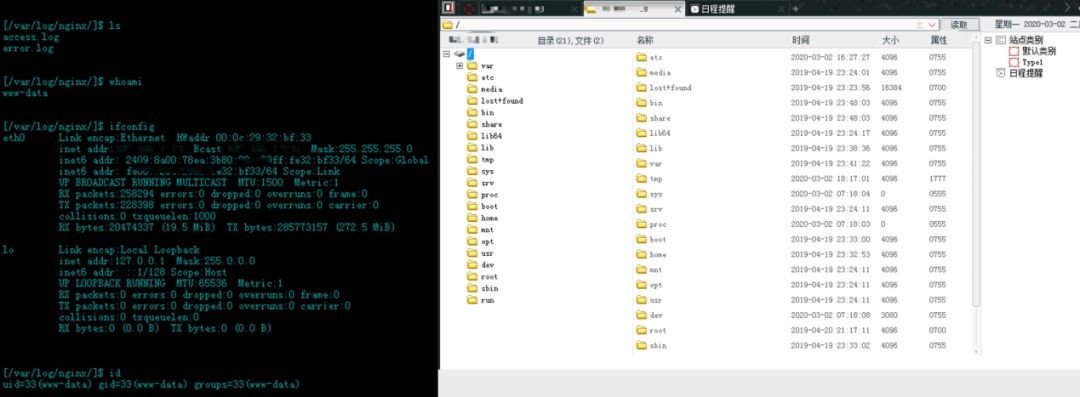
★ Uploading Arbitrary File Vulnerability
Many systems of financial institutions provide file uploading function. In the process of operation, once there is no strict restriction on the type, size, saving path and file name of the uploaded file on the server side, the attacker can easily upload the backdoor program to obtain WebShell, thus controlling the server.
Security Advice from Venustech
It is recommended to use white list verification to filter the uploaded file types. Venusense Intrusion Prevention System (IPS) can be used to detect all kinds of intrusion attacks in time and accurately, and perform real-time and accurate blocking.
★ Command Execution Vulnerability
For the command execution vulnerability, the attacker can execute system commands in the web application due to the insufficient detection of user input commands by web server, thus obtaining sensitive information or taking down the server permissions. More common command execution vulnerabilities occur in various web components, web containers, web frameworks, CMS, etc.
Vulnerability | Risk | InfluencedVersion |
WinRAR has a series of remote code execution vulnerabilities | CVE-2018-20250, CVE-2018-20251, CVE-2018-20252 and CVE-2018-20253 respectively). Using the above vulnerability, an attacker can execute arbitrary code without authorization. | 1. WinRAR software released earlier than Version 5.70 Beta 2. Use the unzip and file management tools of unacev2.dl1 dynamic shared library. |
(CVE- 2019 -14540) FasterXMLjackson-databindremote command execution vulnerability | FasterXML Jackson is a data processing tool for Java of FasterXML Company in the United States. jackson-databind is one of the components with data binding function. Input validation error vulnerability exists in versions ahead of FasterXMLjackson-databind 2.9.10. An attacker can use this vulnerability to execute code. | Jackson-databind<=2.7.9.6,2.8.11.4,2.9.9.3fastjson<=1.2.59 |
CVE-2019-11231) GetSimple CMS remote command execution | In GetSimple 3.3.15 version, attackers can login the background by forging administrator cookies, bypassing authentication, and then write PHP code through the background editing template function module, causing remote code execution vulnerability. | GetSimple<=3.3.15 |
Security Advice from Venustech
It is recommended that financial institutions should update the components and frameworks with vulnerabilities in time. Meanwhile, Venusense Web Application Firewall can be used to defend against attacks targeting at web application vulnerabilities, analyze HTTP/HTTPS flow for web server, and optimize all aspects of Web application access.
With the continuous development of financeand technology, the network security threats in the finance industry tend to be more diversified and complex, which is bound to stimulate more new demands and challenges. As a leading enterprise in the network security, Venustech will continue to uphold its original intention, continue to provide high-quality products and services for the finance users, forge ahead with the industry users, and respond to the challenge.
Have a question? We're here to help.
Please send an email to overseas@venustech.com.cn
Or you can fill out the form below and we will get in touch with you soon.
Thank you for your interest in Venustech.