1. Security Domain Architecture
Security domain design enables users to directly reduce their security risks in information systems. The boundary of a security domain acts as a risk control point. Users can prevent and control risks by establishing an in-depth defense system. Using security domain construction to strengthen internal IT control, IT administrator can clearly know about their assets in protection, the protection levels and measures, and potential threats; therefore, they can deploy new services more easily. Security domain architecture is used as the basis for adopting security technology and business expansion, and is conducive to monitoring security conditions and developing protection strategy systems.
2. Perimeter Security Protection
The unified threat management (UTM) adopts integrated design to fully consider all aspects of access security, and resolves access security problems as a whole. The UTM is an ideal solution for cost-effective, high efficiency, and easy management. It provides comprehensive, real-time security protection for network perimeter and helps users to counter increasingly complicated security threats.
The intrusion prevention system uses a signature- and behavior-based detection method in the detection process, to analyze data packet signature s and effectively identify abnormal access behaviors and data packets in the network.
3. Web Security Protection
The web security protection is mainly applied to analyze the HTTP/HTTPS traffic for Web servers, protect systems from attacks targeting Web application vulnerabilities, and optimize all aspects of Web application access, to improve the availability, performance, and security of Web or network protocol applications and ensure that Web service applications can be delivered quickly, securely, and reliably.
4. Security Auditing and Management
The network security auditing system is designed to parse, analyze, record, and report the system access behaviors of the related staff. It enables users to make prevention plans in advance; perform real-time monitoring and respond to non-compliance behaviors during the process; and prepare compliance reports and trace an accident afterwards. Moreover, it can strengthen the monitoring of internal and external network behaviors and ensure the normal operations of core assets (databases).
The security management platform can obtain information about system security logs or security events and perform comprehensive intelligent analysis on such information. The security events to be analyzed include firewall events, IDS/IPS events, security auditing system events, and other network device and server system events. Based on these security events, the security management platform can use quantitative calculation methods and intuitive charts to display the risk indexes of different IT security domains. It provides a strong data basis for safe operation and maintenance, auditing and assessment of a security system.
5. Security Services
Professional security services allow users to perform an overall assessment on all information systems. Through such assessment and auditing, users can analyze and locate system security risks and weaknesses, develop policies for managing information system security risks, and improve information security management and assurance systems, relevant rules and operation procedures.
Based on the assessment results, users can categorize their information systems into different security levels by following the national standards and security protection requirements for information systems of banking and financial institutions. Depending on the security levels, users can develop different security protection strategies and deploy different security devices to strengthen their systems.
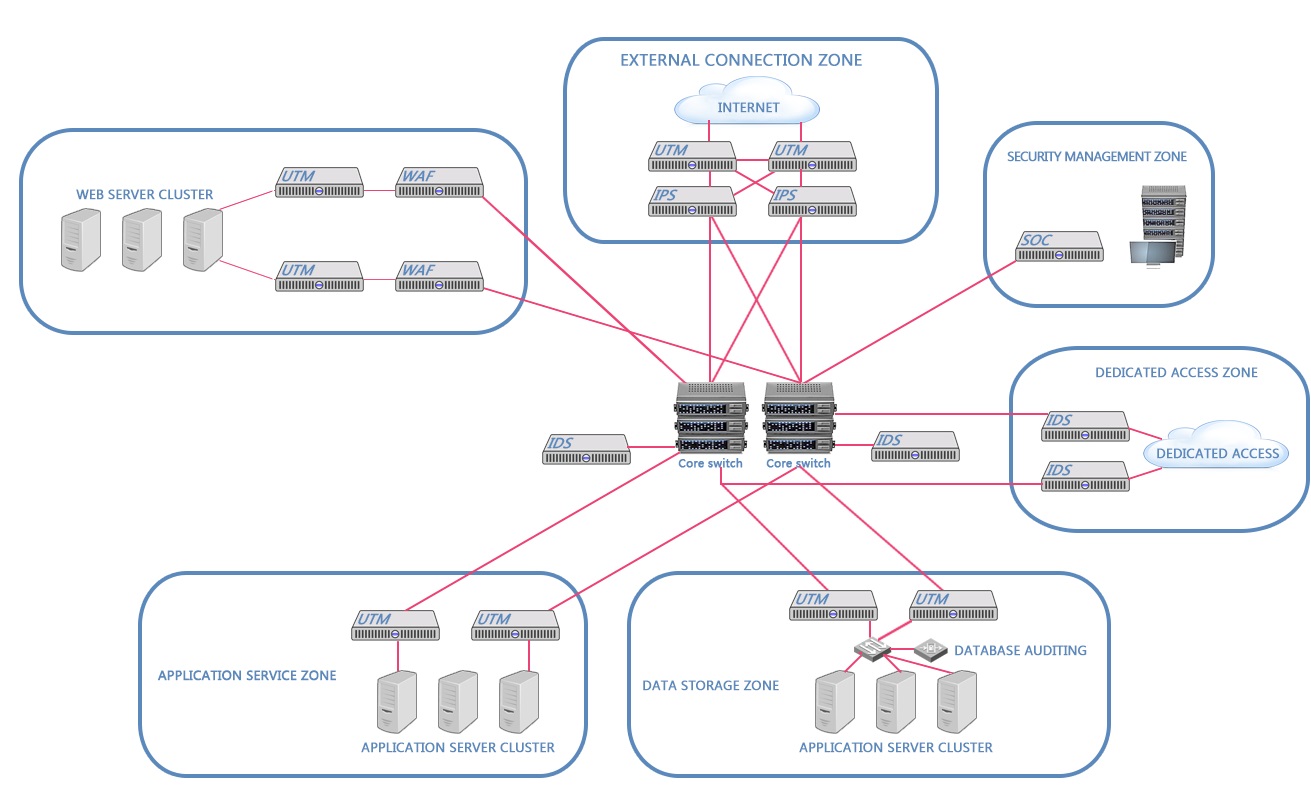
Product Deployment
6. Related Products
Unified threat management (UTM), intrusion prevention system (IPS), intrusion detection system (IDS), web application firewall (WAF), security operations center (SOC), and database auditing.





