Ransomware is a new type of computer virus, which mainly spread in emails, webpages, web vulnerabilities, removable storage. Its main feature is to use various means to deny users access to machines or data, thereby requiring users to pay a ransom.
According to the characteristics of ransomware, it can generally be divided into two categories:
The first is to use technical means to lock the user's machine so that it cannot be accessed. Such ransomware is more common in mobile terminals.
The second is to use a strong encryption algorithm to encrypt user data to make it unusable. This type of ransomware is more common in computers.
No matter which form of ransomware, it has extremely bad properties and great harm. Once infected, it will bring immeasurable losses.
The principle of ransomware invasion
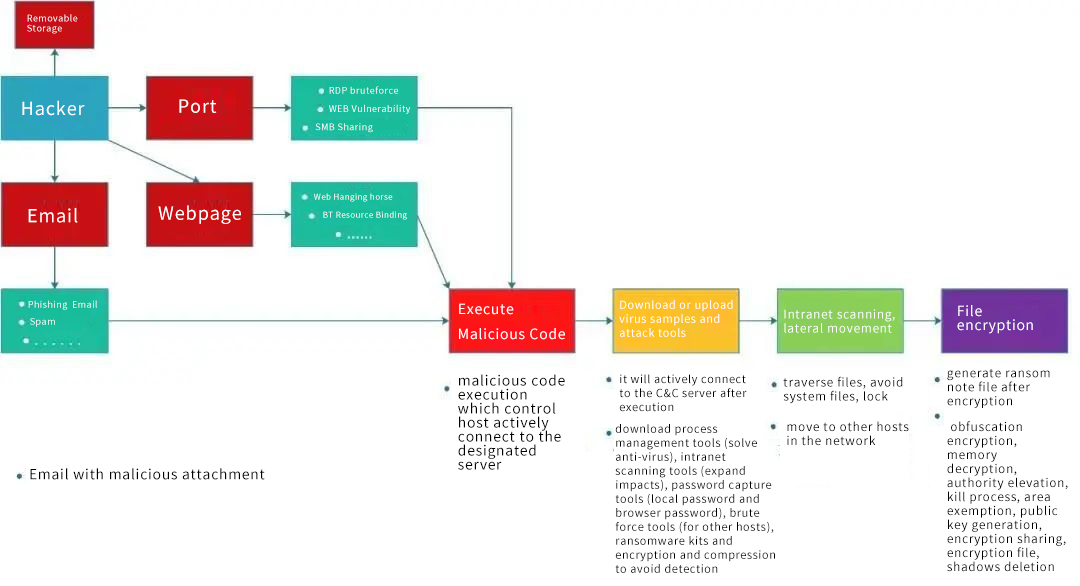
How the Ransomware Spreads
● Send attachments with JS malicious scripts or doc/xls/ppt file macro viruses through spam or phishing emails, etc. Once users open the email attachments, they will be infected.
● Use the form of web hanging horses, Flash hanging horses, or tying Trojan horse programs with resources to spread ransomware. Once the user opens the webpage or downloads and runs the resource, they will be infected.
● Plant a ransomware program in the removable storage and once the user uses it, they will be infected.
● Found vulnerabilities by scanning ports and inserted backdoor programs to perform the next step.
Ransomware Invasion Process
After the user is infected, the hackers run malicious code and control the host to actively connect to the designated server to download the encrypted KEY, process management tools (solve anti-virus), intranet scanning tools (enlarge results), password capture tools (local password and browser password), brute force tools (for other hosts), ransomware kits and encryption and compression to avoid detection. Then, hackers traversed the files, avoided system files, locked important files and moved to other hosts to expand the impacts. After the encryption is completed, a ransom note file is generated, and the desktop is set as a picture that guides the user to pay the ransom.
Ransomware Invasion Features
● Heavy Intentionality
Traditional malicious network behaviors are mostly aimed at destroying networks, servers or terminals, causing network, system or business failure. They are presented in the form of large-scale virus outbreaks. The brakers have no clear targeting, such as CIH viruses, Code Red, Shock Wave, W32.Blaster.Worm, Worm.Whboy, etc. However, a large number of ransomware cases show that intruders have economic demands. The purpose and starting point of the intruder are different, leading to completely different methods used by the intruder.
● Strong Invisibility
Ransomware is often spread through systems frequently used by users such as emails and webpages, and uses ZIP compression packages to bypass traditional virus detection. In addition, ransomware usually mutates very quickly and has strong invisibility.
● Enormous Destructibility
When a terminal in the user's network is infected, the ransomware usually scans the internal network to detect potential intrusion targets. In addition, once encrypted by the ransomware, it is often almost impossible to decrypt.
● Low Cost
The ransom process is usually settled in cryptocurrency. For decentralized network currency, it is extremely difficult to trace the identity of the criminals, so the losses are often not recovered through effective channels. On the contrary, the extremely low cost of crime has led to an increasing number of intruders implementing ransomware.
Security Protection Actuality and Risks
Ransomware is not an advanced persistent threat, boil down to a virus invasion. But why are there still lots of users affected by ransomware? Besides the characteristics of the ransomware itself, it is also closely related to the shortcomings exposed by the current network security construction.
● Traditional Perimeter Security Protection System Collapsed
The current security protection system focuses on the edge However, when boundary defenses are bypassed or intruded, the intranet will be flat to criminals. The malicious behavior of criminals on the intranet cannot be detected by perimeter devices, whether it is intranet scanning, lateral movement or lurking, will cause extremely bad effects on users' network security.
● Common Security Detection Mechanism Failed
The main detection methods of current security equipment are still based on feature detection, and it is difficult to reveal intrusions without known features. The extremely fast mutation speed of ransomware makes it prone to network security incidents for users without effective threat intelligence or advanced threat detection methods, even if security devices are deployed.
● Fragmentation Security Protection Against Blindness
Currently, there are many types of security devices deployed by users, with different vendors, and the amount of log generated by security devices is tremendous. In the face of a great many scattered security information, different interfaces and warning windows of various security products, even experts are often helpless. It is difficult to analyze and find real security risks from massive incidents, and effectively evaluate intrusions behavior, insight into potential threats and the scope of threats.
● Focusing on Construction and Downplay Operation, Is Incapable
The safety protection of most users is attached great importance to during the construction phase, and various defense devices are stacked, but they lack continuous and effective operations after they are deployed. In the event of a ransomware incident, these customers have no preventive measures before the incident, no targeted detection measures during the outbreak, and no timely solutions or methods to solve the problem after the outbreak.
Venustech Ransomware Security Solution
Combining the analysis of the characteristics of ransomware, intrusion principles and the current status of network security construction, Venustech reexamined network security construction and proposed to gradually build risk identification, security protection, security detection, security response and security recovery for users based on the IPDRR architecture. The ability to finally achieve the full process coverage of "before, during and after the incident", meeting the security goals of risk visibility, proactive defense, and automation operation, forming a security closed-loop to ensure user business security.
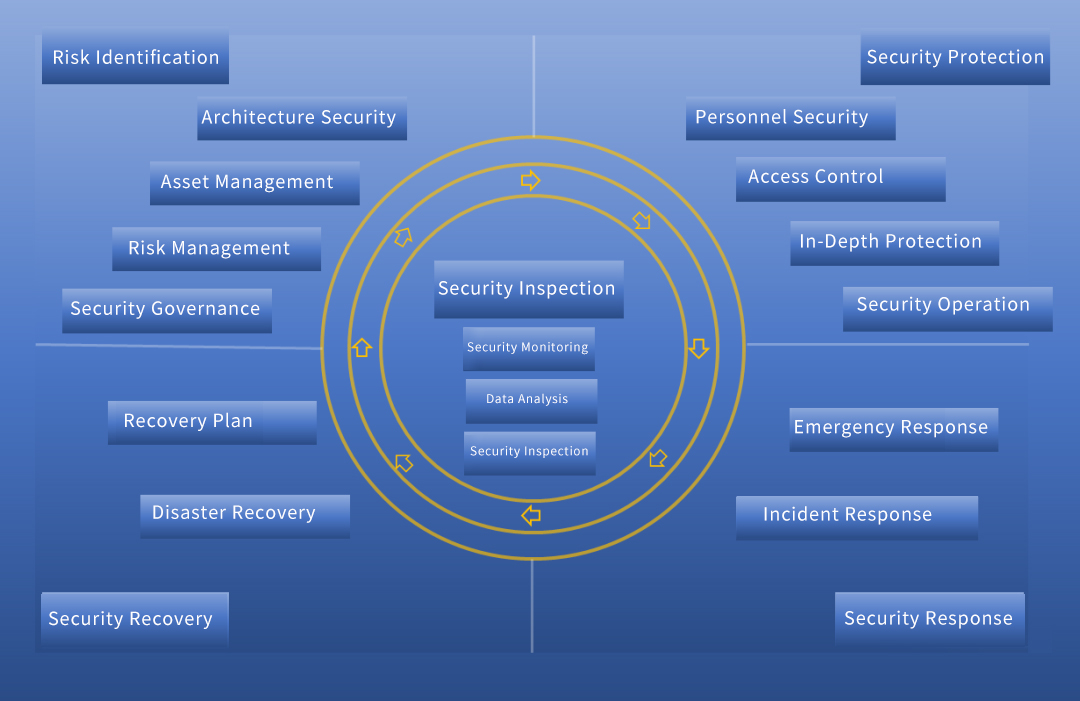
Design Concept
Venustech Ransomware Security Solution combines the core ideas of "One Center, Three Layers of Protection" in classified protection to ensure security construction in five links of identification, protection, detection, response, and recovery from the security area boundary, secure computing environment, and secure communication network.
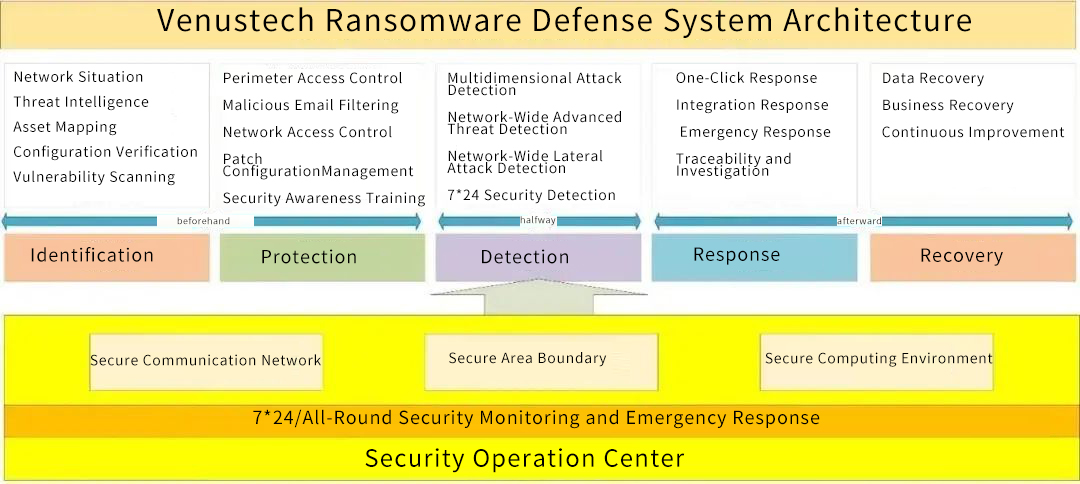
Architecture
● Before-risk identification and key protection
Identification is the foundation of the entire framework, which help organization establish an understanding of network security risks in managing systems, assets, data and capabilities, such as: asset management (organizing assets, clarifying asset information), risk assessment, system vulnerability management, system configuration management, Internet exposure identification (ports, services, etc.), and analysis and prediction of the threat situation of the entire network based on big data correlation analysis technology and threat intelligence empowerment.
Defense is to limit or restrain the potential impact of network security incidents. In addition to identifying risks, focus on security protection to control or reduce the intrusion range. For example: identity and access control, removable storage management, system patch configuration management, malicious email protection, security training, etc.
● During-continuous analysis and full detection
Timely reveal internal threats penetrated defense measures. Establish security detection measures from different dimensions, such as: endpoint security detection, wireless security detection, abnormal network behavior detection, full-flow advanced threat detection, and even east-west traffic detection within the entire network, and perfect uninterrupted security monitoring and analysis system.
● After -fast response and timely recovery
The purpose of the response is to contain the scope of impact caused by a potential network security incident. When a security threat is detected in the network, it will respond as soon as possible to prevent the incident from further expanding. This is divided into two levels. One is to build a coordinated network-wide integration response mechanism through the cloud, network, and endpoint, that is, a threat with entire network response, and full storage of the original session messages; the second is based on professional emergency procedures and security emergency service team further conducted in-depth analysis, traceability, and investigation of the intrusion.
Recovery is to resume normal operations in time to reduce the loss caused by the incident. After completing the analysis and handling of the entire incident, the business data will be restored one by one to ensure the normal operation of the entire business system. For attacks like ransomware, encrypted data is nearly impossible to retrieve except for the payment of ransom. In this way, data disaster recovery may be the only or the final bottom line. Therefore, it is very necessary to use backup tools for data disaster. Finally, repair and improve the entire safety construction system based on each incident to form an overall dynamic closed-loop of the incident.
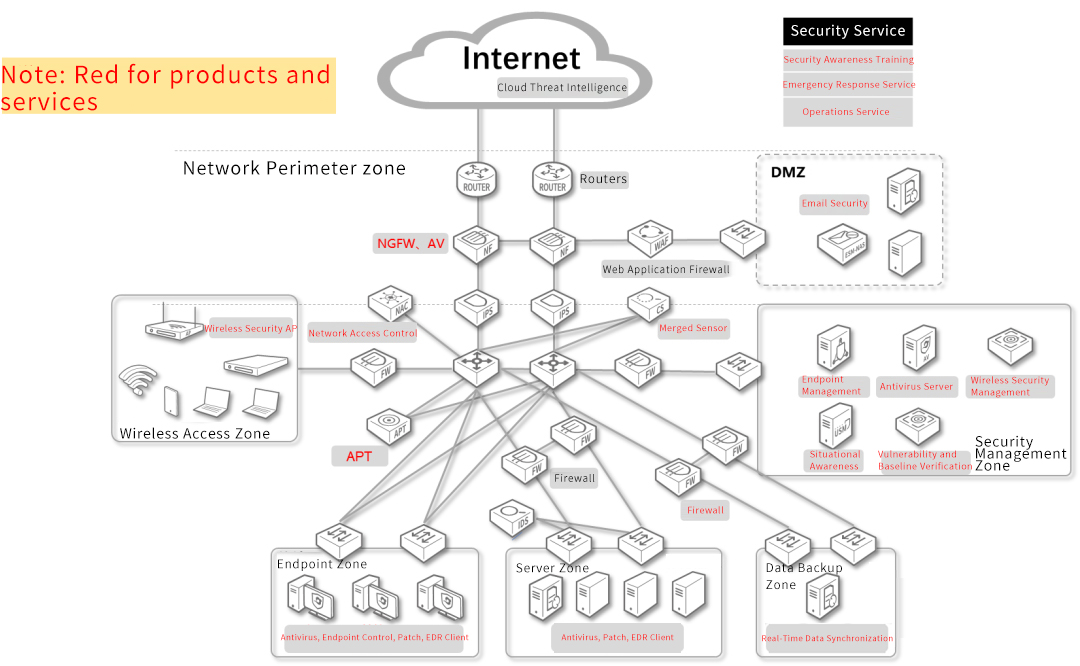
Ransomware Security Solution
● Can't find it
Before, the intrusion area is fully identified, and with the help of threat intelligence, the network-wide situation threat prediction is established to accurately grasp the risk, and block the intruder before the intrusion is launched, so that the intruder is nowhere to be found.
● Can't get in
Before, a series of defense work has been done at the boundaries of the secure area, secure computing environment, secure communication network, security awareness, and other levels to ensure that no matter whether the intruder uses social engineering, brute force, or vulnerability exploitation, it cannot easily break through the internal protection system.
● Can't move
During, at the horizontal and vertical levels, the detection of intrusion threats was carried out, a unified monitoring system was constructed through situational awareness, and professional operations engineers were provided to conduct comprehensive analysis and judgment of incidents in 7*24.
After, based on the coordinated integration response capabilities between the systems, one-click blocking was achieved. Finally, professional emergency response services are used to further analyze the source of the incident and investigate. Ensure that hidden intruders inside the network cannot move or dare to move.
● Can't profit
In hindsight, daily data backup and professional emergency response services ensure that even data that is successfully encrypted by an intruder can eventually be recovered without the need to spend huge sums of money to pay ransoms in the face of great uncertainty. Let the intruder be unprofitable, and the purpose of the invasion is lost.
Have a question? We're here to help.
Please send an email to overseas@venustech.com.cn
Or you can fill out the form below and we will get in touch with you soon.
Thank you for your interest in Venustech.