In the past year or so, various APT attacks, extortion mining incidents, data leakage incidents, and vulnerability attacks have continued to be heard. From the rise of the ATT&CK model framework to the establishment of the realistic attack and defense environment, from the offensive and defense game of deserialization vulnerabilities to the sudden emergence of VPN vulnerabilities, from the ransomware attacks that continue to develop into “APT” to the widespread mining activities, from geopolitical APT attacks to fancy attacks triggered by the pandemic, from the gradual maturity of the MaaS model to the increasing number of cases of “cooperation” between malware families.
In this regard, Venustech Group released the "2019~2020 Cyber Security Situation Observation Report" to try to analyze the cyber security situation and its changes from the whole year of 2019 to the first half of 2020 from the perspective of observers. Hopefully this can be used for various industries and related enterprises as a reference for network security strategy and decision-making.
1.The "ATT&CK" framework continues to heat up, and "Actualized Offensive and Defensive" persistently affects the cyber security industry
Over the past year or so, the ATT&CK framework has been quite popular in the network security industry. More and more network security company have begun to introduce the ATT&CK framework from different dimensions. Both safety research and product integration have found some points, but in terms of product application, ATT&CK still has a far way to go. We firmly believe that under the background of the continuous improvement of detection technology in the future, ATT&CK will definitely become a weapon for security products to achieve attack chain restoration.
2.Deserialization vulnerabilities have become the primary threat to Web attacks, and gateway-type vulnerabilities such as VPN have become new attack entrances
For the whole year of 2019, the total number of security vulnerabilities recorded in Venustech was 15,046, among which ultra-risk vulnerabilities and high-risk vulnerabilities increased by 67% and 49% year-on-year respectively. Two characteristics are particularly worth noting: First, deserialization vulnerabilities have gradually become the main threat of Web vulnerabilities; second, the emergence of gateway vulnerabilities such as VPNs.
Top 10 Popular Vulnerabilities of 2019~2020 H1 |
“Eternal Blue" series |
CVE-2017-11882/CVE-2017-0798 |
CVE-2018-20250 |
CVE-2017-0199 |
CVE-2019-2725/2729 |
CVE-2019-19781 |
CVE-2017-17215 |
CVE-2017-5638(S2-045) |
CVE-2019-11510 |
CVE-2012-0158 |
3.The dark web underground market is is developing rapidly and gaining maturity, and the malware family tree systems for “Collaborative Engagement”
The dark web underground market under the Malware-as-a-Service (MaaS) model has become more mature, and has formed a complete system from malicious code writing, malicious code evasion, malicious code hosting to malware distribution.
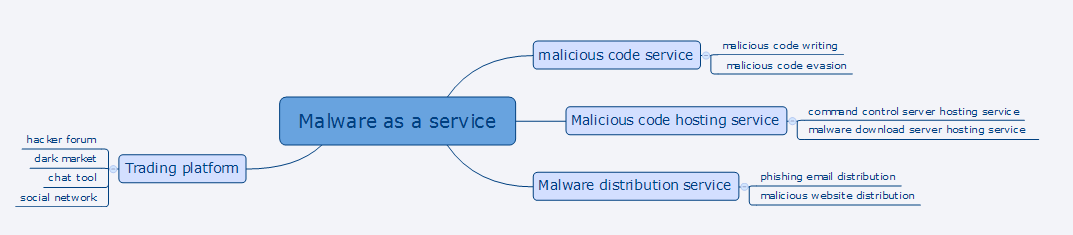
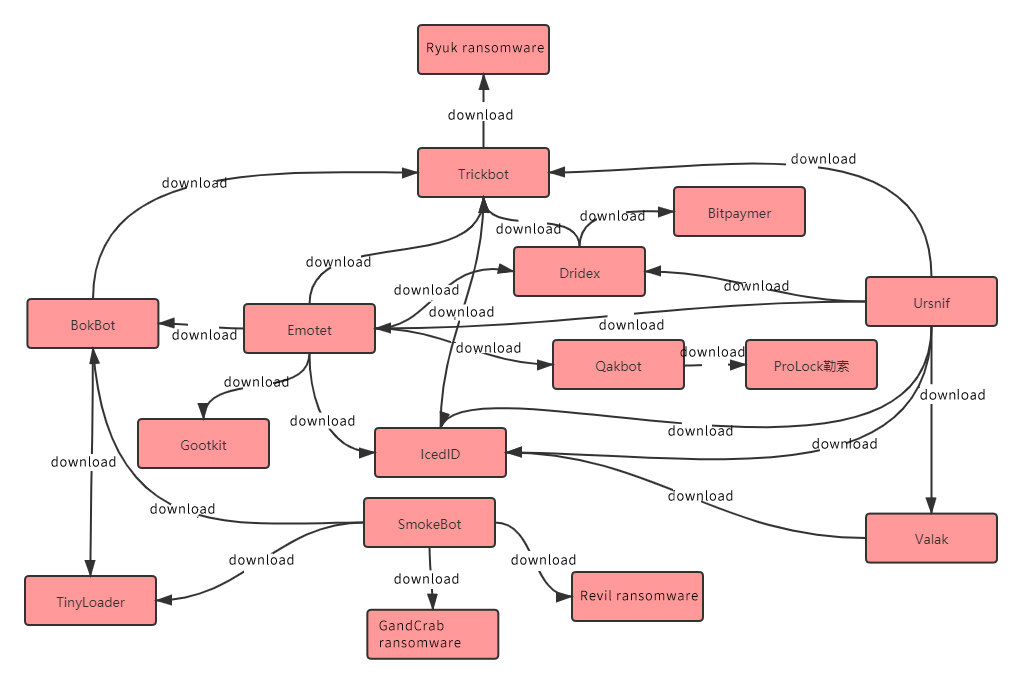
Under the MaaS model, we have observed that different groups use the same malware to carry out "different" attacks. The same malware also performs different functions in different attacks.
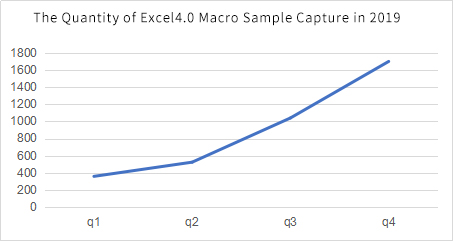
4.In recent years, few high-risk vulnerabilities in Office have appeared. Unconventional and effective attacks are of more concern.
Since the outbreak of a large number of Office 0day vulnerabilities in 2017, there has been no new attack method that uses simple and powerful functions like the formula editor vulnerabilities in the past two years, and the attack techniques used by malicious samples have not changed significantly. In the process of offensive and defensive confrontation, attackers gradually began to try to use uncommon file types and some forgotten unpopular features in Office (such as Excel 4.0 macros) as attack vectors, and reuse the original attack code at a lower cost to bypass detection.
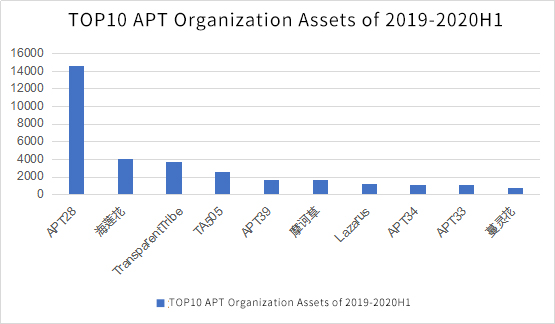
5.Geopolitical relations have led to the intensification of APT attacks. The leak of APT attack weapons leads to the commodity of cyber arms
When dealing with irreconcilable geopolitical conflicts, APT attacks are currently the most concealed and effective attack method besides military strikes. More and more governments have begun to form national-level APT attack organizations. As long as there are political goals and economic benefits, APT attacks will not stop. In the past year or so, there have been many APT attacks related to geopolitical conflicts in South America, the Middle East, and Northeast Asia.
In addition, the usage of APT attack weapon has g evident generalization trend. In the past year or so, there have been many incidents of APT organization tool and code leaks in the Middle East, which has further result in the generalization trend of APT attack weapons usage and the commodity of cyber arms.
6.Ransomware attacks trend to "APT" and are gradually targeting large and powerful value-oriented goals
Over the past year or so, ransomware attacks have gradually evolved from the widespread and purposeless spreading in 2014 and the large-scale automated spreading by WannaCry in 2017 to the human-centric "APT" attack stage. The targets of attack objects are no longer limited to small and medium-sized enterprises, but large corporate who are more capable of paying the ransom. Even if the ransom is not received, the attacker will try to conduct a secondary blackmail by leaking the victim's confidential documents.
We expect that in the future, ransomware attacks will further develop in the direction of "specialization and precision". "Specialization" means that large-scale ransomware attacks may be difficult to reproduce or short-lived. Attackers will more consider the choice of attack targets from the perspective of attack cost and rate of return; "Precision" means that the attackers may be customize special ransomware to increase the success rate of attacks.
7.Network offensive and defensive security drill and cyber range construction are in full swing, talent training and the construction of offensive and defensive environment are highly valued
The essence of cyberspace security is confrontation. With the continuous improvement of the technical strength of network attackers, the network attack surface continues to expand, and the number of attack incidents is constantly increasing, and users continue to emerge demand for the construction of network attack and defense confrontation. The common solution is to strengthen the training of talents, improve the basic infrastructures of offensive and defensive support, hold red and blue offensive and defensive security drills, and build a cyber range with industry characteristics.
Over the past year or so, government and enterprise customers have paid more attention to the construction of cyber ranges, thereby enhancing the cyber security knowledge and technical capabilities of practitioners and realizing a leap in cyberspace confrontation capabilities.
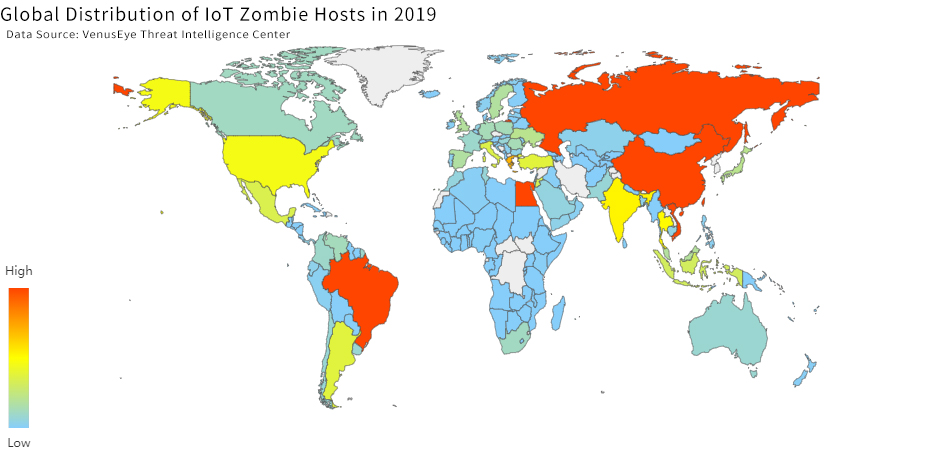
8.Internet of Things (IoT) botnets continue to proliferate, and China is the biggest victim of IoT botnets.
2019 is the twentieth year of the concept of the IoT, which has deeply affected various industries such as agriculture, medical and industry. With the rapid development of the IoT, its security issues have also received increasing attention. A large number of cameras and routers exposed on the Internet have become a coveted horserange for hackers.
According to data from the VenusEye Threat Intelligence Center, in the past year or so, China still has the largest number of IoT devices controlled by botnets, and has opened a significant gap from the second place.
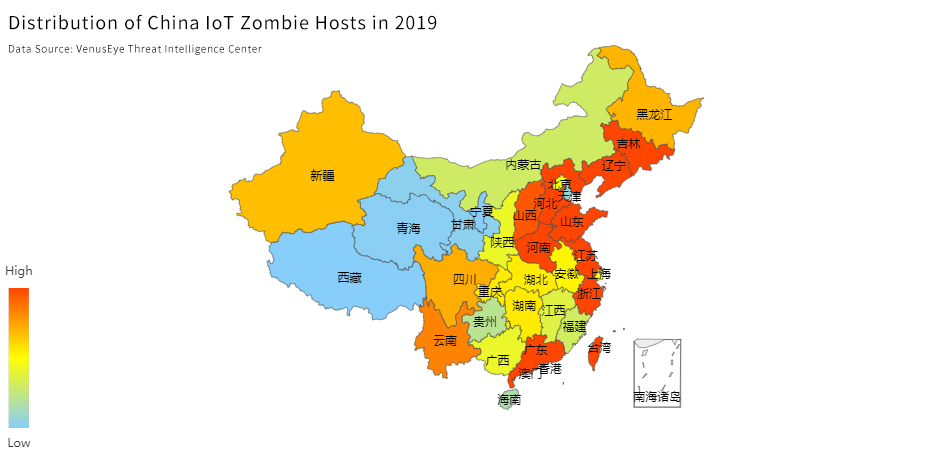
The five regions with the most IoT zombie hosts in China are Henan, Shandong, Liaoning, Jiangsu and Zhejiang.
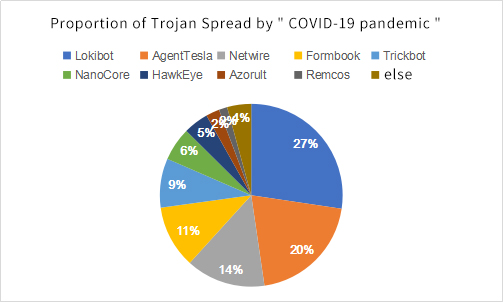
9.'COVID-19 Pandemic'has become the hottest topic, hackers launch all-round attacks
COVID-19 breakout in early 2020 has spread to almost every corner of the world, seriously affecting global economic and social development. Some hackers took this opportunity to use hot information to launch attacks. The uncertainty of the pandemic and people’s fear have created a golden opportunity for attackers.
In the past few months, we have observed a variety of cyberattacks using the COVID-19 pandemic. Active APT organizations such as Patchwork, Ocean Lotus, BITTER, TA505, Lazarus launched phishing attacks using "coronavirus prevention" and "pandemic report" as bait; various cyber gangs are also ready to move, through "reform" known Trojan for attacks.
In the face of unprecedented challenges and opportunities, Venustech is willing to work together with peers to promote the development of the cyber security industry, strengthen the construction of independent core technology capabilities, in order to enhance network security capabilities and continue to contribute to the next golden decade of network security.
Have a question? We're here to help.
Please send an email to overseas@venustech.com.cn
Or you can fill out the form below and we will get in touch with you soon.
Thank you for your interest in Venustech.